Verse of the Day
"You are already clean because of the word I have spoken to you. Remain in me, as I also remain in you. No branch can bear fruit by itself; it must remain in the vine. Neither can you bear fruit unless you remain in me." John 15:3-4
Short Reflections
Before I dive into NSX, I wanted to write briefly about the verses I read this morning. The verses come from the book of John, one of the four gospels that writes about Jesus's life and teachings firsthand. What is profound about those verses is that because Jesus knows God the father and has already spoken over us, we are clean and brought into God's love. We did nothing to earn God's love, but Jesus still calls us clean for those who "remain in him." Thank God that salvation is not earned!
Virtualization 101 🖥
Network virtualization is an interesting, but complex topic that is confusing for most. When I first started learning about it, I became overwhelmed by its sheer complexity of it. To help us understand what it is, I think it is important to recap the history of virtualization and WHY virtualization in the first place.
Virtualization is using software on hardware such as servers or storage arrays to manipulate the hardware into running more efficiently. In the case of server virtualization, before virtualization, individual servers could only run a few applications. If a business wanted to expand workloads, new servers had to be procured, rack-stacked-cabled, and configured to support that workload. This process led to unused computing resources and inefficient server usage. Virtualization solved this issue by allowing one server to run virtual servers on top of it. Now instead of buying a new server to support one application, the IT team could create a logical server with a few clicks on the existing infrastructure.
Compute virtualization came first but was followed by storage virtualization. Storage virtualization used software to allow storage drives on different appliances to be pooled together into one logical datastore. The benefits were similar to compute virtualization including better utilization of existing infrastructure and faster performance for storage read/write I/O.
The last piece of virtualization in the core infrastructure stack was the network. Companies like Cisco and Nicira (acquired by VMware) would revolutionize the software-defined data center (SDDC) by using software to virtualize network deployments, IP/security services, and extend networks past the physical boundaries that were used to confine them.
OKAY, BUT WHAT DOES THAT EVEN MEAN
I won't get into all in this post because it requires a fundamental grasp of network fundamentals like VLANs, subnets, and NAT, but in essence, the same benefits that are seen in virtualization as a whole are seen in network virtualization: less hardware equals less maintenance which also means quicker deployment times.
What is VMware NSX?
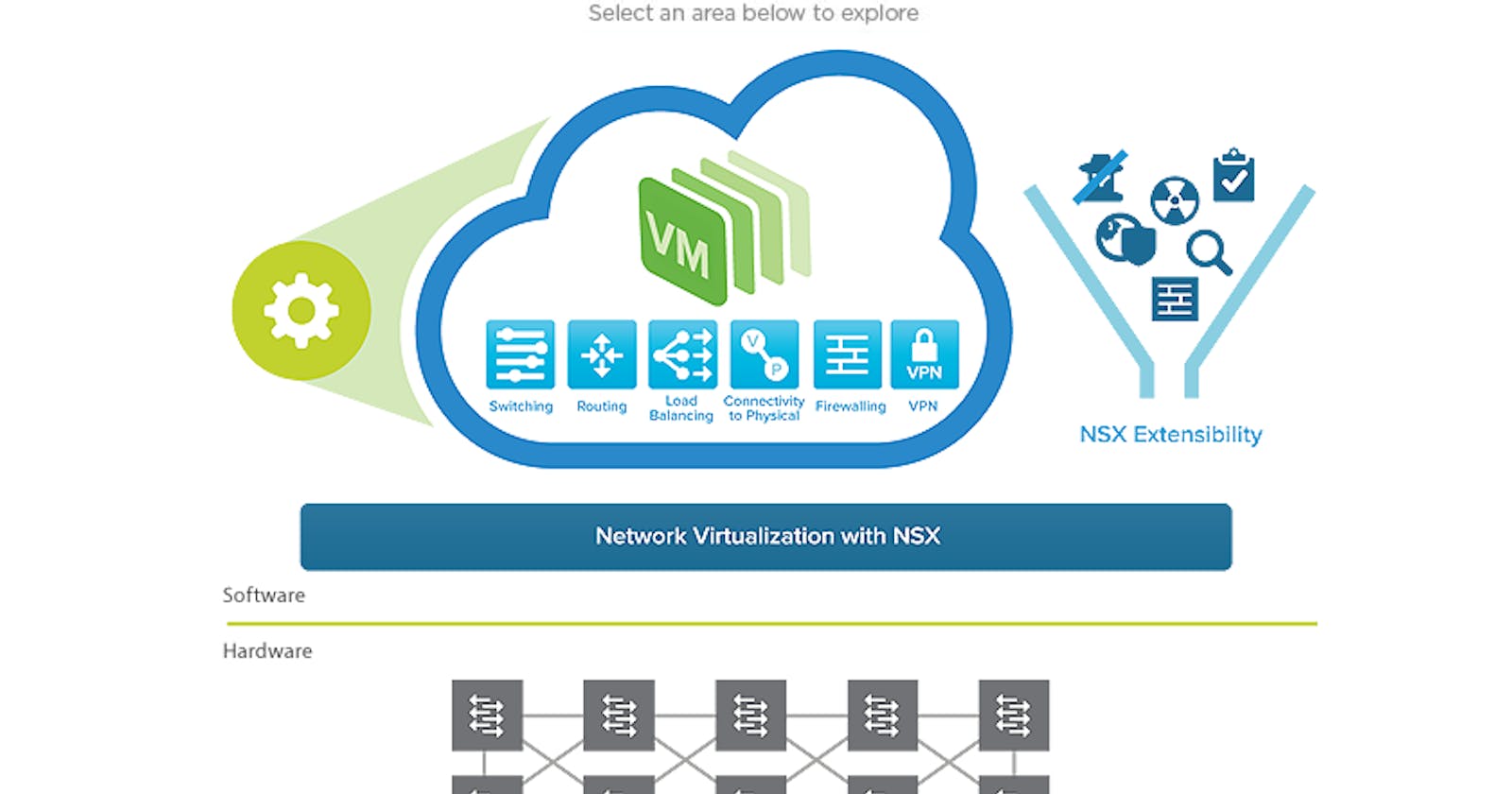
NSX is a powerful VMware networking application that lets IT teams take advantage of virtualization benefits like consolidated management and faster deployment times. This is done by virtualizing switches, routers, firewalls, VPNs, load balancers, and more. Before network virtualization, each of those items was physical appliances that had to be configured. NSX allows for those services to run as software instead. The key components that I will focus on are logical routing/switching and microsegmentation.
NSX Switching & Routing 🌐
Logical switching and routing is performed to save precious network bandwidth and allow for identical VLANs and subnets to exist at multiple physical sites. The benefit of this can be understood when we think about the limitations of switches and routers. Switches can support up to 4096 VLANs and cannot send traffic between different VLANs without the use of a router or an L3 switch. 4096 VLANs may seem like a lot, but when you consider how interconnected the world is and the demand for data, those VLANs can quickly become depleted. Furthermore, since data going to different VLANs needs to be routed, packets in virtualized environments would still have to hit the physical uplinks of servers and traverse the physical network even if two VMs communicating with each other lived on the same physical host. This meant more network congestion and less available bandwidth.

~this picture probably doesn't make sense, but credit to VMware Blogs~
NSX introduced the concept of the routing services running in the hypervisor for local host routing. Furthermore, routing could be done between different hosts by overlaying a Layer 2 domain on a Layer 3 network. Let's take the first scenario of a VM communicating with another VM on the same host but in different networks. Before NSX, that VM traffic would have to go out of the physical NIC of the server and reach the upstream router or L3 switch before being sent back down to the same host. NSX enabled the physical host to take care of inter-VLAN routing in-kernel (hypervisor level). Routing no longer had to reach the physical network. The process above took care of the intra-host situation, but what happens when a packet needs to reach a VM on a different host?
When considering what the routing process looks like when a VM is communicating with another VM on a different host, NSX has you covered. NSX can have the same VLAN/subnet existing on two separate hosts, extending that L2 domain. This means greater private IP preservation for multi-tenancy use cases. NSX can do this using GENEVE (or VXLAN) encapsulation, which encapsulates the original VM data with a Tunnel Endpoint (TEP) IP address. Every host participating in the NSX network has a unique TEP IP, thus allowing the router to know which host the destination VM is at. Without the additional encapsulation, L2 boundaries could not co-exist across different hosts or physical sites.
NSX Microsegmentation 🔐
Microsegmentation is the process of isolating east-west traffic or communication between VMs. This is performed by creating security policies based on what segment a VM resides in, meaning in a three-tier application, the web, app, and DB VMs may reside in three different segments. The VMs can be isolated from each other using IP addresses, user contexts, and unused ports/protocols.
By doing this, the IT team can fulfill zero-trust standards that are seen in modern cybersecurity environments. Coincidentally, Microsegmentation is the most adopted feature of NSX because it takes less time to deploy than the overlay networking process above. Microsegmentation, or the distributed firewall, can be configured all from NSX and used on the existing physical network without having to make any changes.

Concluding Thoughts
Since the product's release by VMware in 2013, many iterations have come and gone. For example, it was once only offered for vSphere environments but then opened up to other ecosystems. VMWare then announced a deprecation and migration from the vSphere only, NSX-V, to the KVM supported, NSX-T. VMware probably decided this wasn't the most profitable decision because, in Aug 2022, NSX-T version 4.0 would be named just NSX and would no longer support KVM based hypervisors. How do we keep up with technology if it is always changing on us?! 😡
Lastly, there are more capabilities that NSX can do than what I described, but I'll leave it up to the vExperts to show you all the cool diagrams 👀